Remote LAN Access with Tunneled Outbound using WireGuard
This is a quick follow up (after 2 years still counts right?) on my previous post about Remote LAN access with WireGuard.
In the previous episode, we had the following setup:
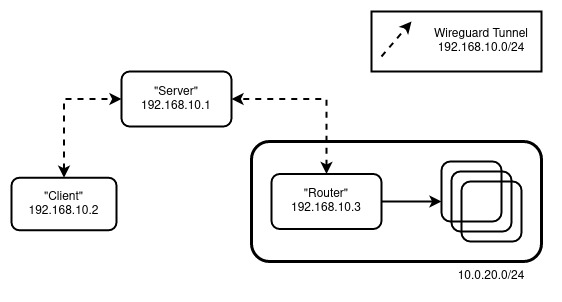
My main issue with this is that I lose privacy when accessing the general internet. We remedy this by doing:
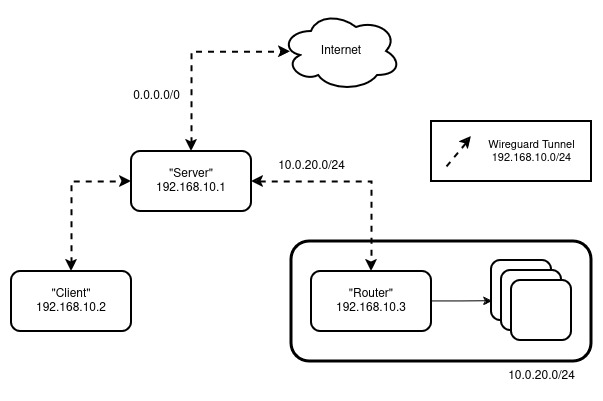
So now, any non-homelab traffic gets tunneled through the server instead of originating from my client.
Updated “Server” Config
To support the additional 0.0.0.0/0 outbound, we update the server config to:
[Interface] |
Don’t forget to update eth0 and 10.0.20.0/24 with your setup.
Updated “Client” Config
To force the “Client” to tunnel all requests to the “Server”, we update the client config to:
[Interface] |
The DNS here can either be a public one or within your homelab (10.0.20.0/24).
Bonus: UFW
If you are using ufw, you can update your settings with the following:
ufw allow 51820 |